At Ferrara IT, we deliver fully integrated Managed IT and Managed cybersecurity solutions as a Managed Services Provider (MSP) and Managed Security Services Provider (MSSP). Our security-first approach combines advanced tools, proactive threat detection, rapid incident response, and compliance-focused risk assessments—designed to protect your business, reduce risk, and keep you audit-ready.
Managed Cybersecurity Services for Security-Driven Organizations
PROTECT YOUR DATA • STAY COMPLIANT • RESPOND WITH CONFIDENCE
overview
End-to-End IT Management & Cybersecurity from a Trusted MSP & MSSP
approach
Our Multi-layered Approach to Cybersecurity
Our multilayered cybersecurity framework ensures end-to-end protection, covering everything from endpoint security to advanced threat detection and response. Each layer reinforces the next, creating a robust security posture that safeguards your business from evolving threats.
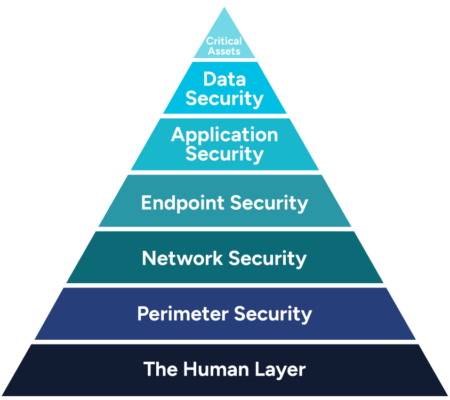

The Human Factor
People are your first line of defense—and often your weakest link. Our on-going employee security training, simulated phishing tests, and AI email filtering empower your team to detect and block threats.

Perimeter Security
We utilize next-gen firewalls and intrusion prevention systems that block unauthorized access, malware, and DDoS attacks. Secure remote access and network segmentation further ensure employees access only what they need while isolating critical systems to limit internal threats.

Network Security
Once inside your network, attackers try to move laterally, but our 24/7 SOC, SIEM analysis, and MDR services stop them before they reach critical systems. We continuously monitor and analyze activity to detect and neutralize threats before they escalate.

Endpoint Security
Every laptop, desktop, mobile device, and BYOD is a potential gateway for cyberattacks. Our AI-driven endpoint detection and automated patch management work together to secure every device in real time.

Application Security
Your cloud apps (Microsoft 365, Azure, AWS, and SaaS) require robust security to prevent unauthorized access and data breaches. We use continuous cloud posture management to fix vulnerabilities, enforce MFA and identity protection, and monitor the dark web for compromised credentials.
A strong security strategy is essential for business continuity—preventing cyber threats, reducing downtime, and ensuring compliance. Learn more in our blog: How Managed Security Services Support Your Business Continuity Strategy
overview
Our Comprehensive Cybersecurity Solutions
Security Solutions
Threat Detection & Response
Enhance your security posture with our comprehensive suite of threat detection and response services:
- Endpoint Detection & Response (EDR): Advanced threat protection for endpoints with real-time monitoring and immediate response.
- MDR & XDR: 24/7 expert-driven security monitoring, incident response, and proactive threat hunting that consolidates data across endpoints, networks, and cloud environments for a holistic defense.
- 24/7 Security Operations Center (SOC): A dedicated, round-the-clock operations center that continuously monitors, identifies, and coordinates rapid incident response to emerging threats.
- Security Information & Event Management (SIEM): Centralized log management, real-time threat detection, and compliance reporting. Read our blog: Why every company needs MDR and SIEM and how they work together


Security Solutions
Identity & Access Security
Ensure only the right individuals gain secure access to your critical resources.
- Privileged Access Management (PAM): Secure control over administrative accounts using least privileged, just-in-time access to prevent unauthorized access.
- Identity & Access Management (IAM): Streamlined user authentication, authorization, and identity governance.
- Zero Trust Security: Continuous verification of users and devices to eliminate implicit trust.
- Single Sign-On (SSO) & Multi-Factor Authentication (MFA): Enhanced authentication security across all enterprise systems. Read our blog: The importance of enforcing MFA
Security Solutions
Network & Endpoint Protection
Strengthen your digital defenses with our comprehensive network and endpoint protection solutions:
- Firewall Management & Intrusion Prevention (IDS/IPS):
Defend your network from unauthorized access and cyber threats. - Patch & Vulnerability Management:
Keep your systems up to date and secure against known exploits. - Data Loss Prevention (DLP):
Safeguard sensitive information by preventing unauthorized data access and leakage. - Email Security & Anti-Phishing Protection:
Shield your organization from phishing attacks, business email compromise, and malware.


Security Solutions
Cloud & Infrastructure Security
Protect your digital environment with our advanced cloud and infrastructure security solutions designed to enforce best practices, control data access, and mitigate cyber risks.
- Cloud Security Posture Management (CSPM): Enforce security best practices across Azure, AWS, and Google Cloud.
- Cloud Access Security Broker (CASB): Control data security and manage access across cloud applications.
- Microsegmentation & Network Segmentation: Isolate critical systems to minimize the impact of cyber attacks.
- Workload & Container Security: Protect virtual machines, containers, and cloud-native applications.
How We Can Help
Every business has unique security needs. Whether you’re just starting to build a cybersecurity strategy or need fully managed protection, Ferrara IT can help.

Strategy Development
Get a customized security recommendation roadmap that aligns with your business objectives and risk profile.

Implementation Support
Get expert implementation of advanced security solutions to protect your business.

On-Going Management
Rely on our team for on-going 24/7 threat monitoring, rapid incident response, and continuous protection.
Assessments
Understand Your Risks With Our Risk Assessments
As cyberattacks continue to rise, identifying your security gaps is crucial for protecting your business. Our comprehensive IT assessments uncover vulnerabilities, inefficiencies, and compliance gaps before they turn into costly problems, and in addition to the assessments listed below, we offer many others.
Microsoft Cloud Risk Assessment
Uncover risks within Microsoft 365 and Azure AD. Obtain a risk score and actionable recommendations based on Microsoft best practices.
Network Risk Assessment
Analyze on-premise Active Directory and LAN for misconfigurations and best practice violations. Reports provides actionable solutions.
Cyberattack Risk Assessment
Identify hidden vulnerabilities that could be exploited by a successful phishing attack or attackers who has managed to breach your firewall.
Penetration Testing & Report
Simulate real-world cyberattacks to uncover vulnerabilities in networks, cloud and applications. Strenghten security, and reduce risk.
Not sure which assessment is right for you? Explore our full range of risk assessments to identify security gaps and protect your business.
Benefits
Why Businesses Choose Ferrara IT for Cybersecurity
Let’s strengthen your security today. Get Started.

Customer Testimonial
"SINCE PARTNERING WITH FERRARA IT, WE HAVEN'T HAD A SECURITY INCIDENT IN YEARS"
“We used to struggle with malware and security breaches, but Ferrara IT implemented advanced security solutions that changed everything. They continuously bring us the latest technology to keep our business protected and conduct regular employee security training to ensure our team remains vigilant against cyber threats.”
Non-Profit Organization
Let's Strengthen Your Security
Schedule A Security Consultation To Discuss Your Needs
We know there are many IT companies out there, but at Ferrara IT, we do things differently. With a strategic, honest, and security-first approach, we prioritize your business needs and long-term success. Schedule a call and see the difference for yourself.
What to Expect?

Step 1: Discovery Call
Let’s talk! We’ll discuss your IT challenges, business goals, and security needs to understand how we can help.
Step 2: Free Consultation
Our experts will evaluate your IT environment and uncover opportunities for optimization.
Step 3: Tailored Proposal
Within a week, we’ll provide a custom IT security proposal designed to align with your business goals.
We'll Get In Touch Within 1 Business Day!